
Introduction
SPF (Sender Policy Framework) is a DNS text record that specifies which servers are allowed to send email for a domain. Since SPF is a DNS entry, it ensures that only domain owners or administrators can add or modify the list of authorized servers.
Here’s how SPF works:
The receiving mail server fetches the HELO message and sender address.
It then performs a TXT DNS query for the SPF record of the claimed domain.
The SPF record is used to verify the sender server.
If the verification fails, the sender server receives a rejection message.
DKIM (DomainKeys Identified Mail) verifies that the content of a message hasn't been altered since it left the originating mail server. This is done through public/private key signing:
The domain owner adds a DNS record with the public DKIM key.
The sender server signs outgoing messages with a private key.
The last server in the domain’s infrastructure checks if the domain in the "From:" header is in its "signing table." If
not, the process stops.
A "DKIM-Signature" header is added to the message using the private key.
The message content must remain unchanged to ensure the DKIM header remains valid.
Upon receipt, the receiving server performs a TXT DNS query to retrieve the public key and verify the DKIM signature, helping determine if the message is trustworthy.
Setting Up SPF
To set up SPF, add a TXT record to your DNS zone for your domain. This can be done through your domain registrar's interface or your own nameservers if you manage them. Here’s a basic SPF TXT record:
"v=spf1 a mx -all"
Ensure the double quotes are included. For more complex configurations, refer to the SPF documentation.
Setting Up DKIM
Setting up DKIM involves a few more steps but is manageable if you’re using a Postfix mail server on Ubuntu. Follow these steps:
1. Install Required Packages:
apt-get install opendkim opendkim-tools -y
2. Configure OpenDKIM:
nano /etc/opendkim.conf
Add:
Domain your_domain
KeyFile /etc/postfix/dkim.key
Selector dkim
SOCKET inet:8891@localhost
- Edit /etc/default/opendkim:
nano /etc/default/opendkim
Add:
`SOCKET="inet:8891@localhost"
3. Configure Postfix:
- Edit /etc/postfix/main.cf:
nano /etc/postfix/main.cf
- Ensure these lines are present and not commented out:
milter_protocol = 2
milter_default_action = accept
If you have other filters (SpamAssassin, Clamav, etc.), append the OpenDKIM milter to smtpd_milters and non_smtpd_milters:
smtpd_milters = unix:/spamass/spamass.sock, inet:localhost:8891
non_smtpd_milters = unix:/spamass/spamass.sock, inet:localhost:8891
If not, define:
smtpd_milters = inet:localhost:8891
non_smtpd_milters = inet:localhost:8891
4. Generate Public and Private Keys:
opendkim-genkey -t -s dkim -d your_domain
Move the private key:
mv dkim.private /etc/postfix/dkim.key
Restart the services:
service opendkim start
service postfix restart
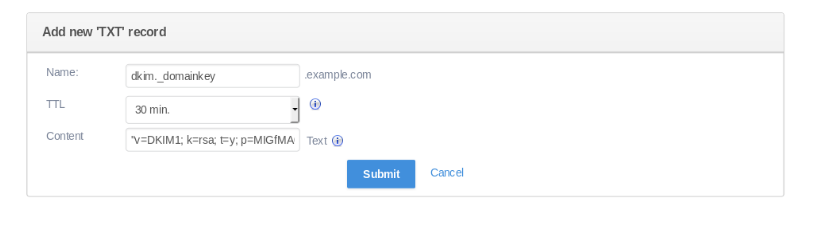
5. Add the Public Key to DNS Records: Find the public key in dkim.txt:
cat dkim.txt
Add this information to your DNS records.
6. Sharing DKIM Keys for Multiple Domains: If you’re serving multiple domains, update /etc/opendkim.conf:
Domain *
KeyFile /etc/postfix/dkim.key
Selector dkim
SOCKET inet:8891@localhost
Testing
Allow some time for DNS changes to propagate before testing. A good tool for testing is Mail Tester.