Introduction to DKIM
Curious about how DKIM works? DKIM (DomainKeys Identified Mail) is a method to verify the trustworthiness of email content, ensuring it hasn't been altered since leaving the original mail server. It adds an extra layer of credibility by using a public/private key signing process. Here's how it works:
1. Key Generation: The domain owner creates a public DKIM key and adds it to their DNS records. This key is used by recipients to verify the DKIM signature on incoming messages.
2. Signing: The sending server signs outgoing messages with its private DKIM key. If the domain in the "From:" header is in the server’s "signing table," a "DKIM-Signature" header is added to the email using the private key.
3. Verification: Upon receipt, the receiving server checks the DKIM-Signature by querying the DNS for the corresponding public key. If the signature matches, the message is deemed trustworthy.
It's similar to an SSL certificate, where a private key signs messages and a public key, stored in DNS, verifies the signature.
Update System
Before diving in, ensure your server is updated. Also, use a screen session for stability:
screen -U -S opendkim-screen
yum update -y
Enabling EPEL Repository
OpenDKIM is available in the EPEL repository. Enable it with these commands:
wget -P /tmp http://mirror.pnl.gov/epel/6/i386/epel-release-6-8.noarch.rpm
rpm -Uvh /tmp/epel-release-6-8.noarch.rpm
rm -f /tmp/epel-release-6-8.noarch.rpm
Installing OpenDKIM
Install OpenDKIM using:
yum install opendkim -y
Configuring OpenDKIM
Backup and edit the OpenDKIM configuration file:
cp /etc/opendkim.conf{,.orig}
nano /etc/opendkim.conf
Add or update the following settings:
AutoRestart Yes
AutoRestartRate 10/1h
LogWhy Yes
Syslog Yes
SyslogSuccess Yes
Mode sv
Canonicalization relaxed/simple
ExternalIgnoreList refile:/etc/opendkim/TrustedHosts
InternalHosts refile:/etc/opendkim/TrustedHosts
KeyTable refile:/etc/opendkim/KeyTable
SigningTable refile:/etc/opendkim/SigningTable
SignatureAlgorithm rsa-sha256
Socket inet:8891@localhost
PidFile /var/run/opendkim/opendkim.pid
UMask 022
UserID opendkim:opendkim
TemporaryDirectory /var/tmp
Setting Up Public/Private Keys
Generate keys for your domain:
mkdir /etc/opendkim/keys/your_domain.com
opendkim-genkey -D /etc/opendkim/keys/your_domain.com/ -d your_domain.com -s default
chown -R opendkim: /etc/opendkim/keys/your_domain.com
mv /etc/opendkim/keys/your_domain.com/default.private /etc/opendkim/keys/your_domain.com/default
Update the OpenDKIM key table:
nano /etc/opendkim/KeyTable
Add:
default._domainkey.your_domain.com your_domain.com:default:/etc/opendkim/keys/your_domain.com/default
Update the signing table:
nano /etc/opendkim/SigningTable
Add:
*@your_domain.com default._domainkey.your_domain.com
Update the trusted hosts:
nano /etc/opendkim/TrustedHosts
Add:
127.0.0.1
your_domain.com
your_servers_hostname.com
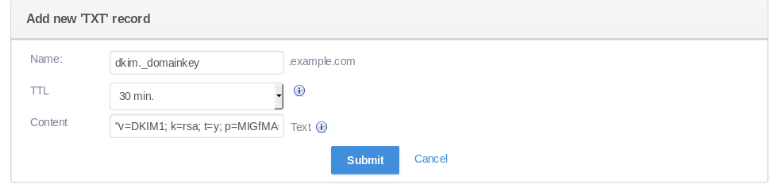
Adding the Public Key to DNS Records
Add the public key to your domain’s DNS records. This process varies depending on your DNS management tools. You can find the public key in:
cat /etc/opendkim/keys/your_domain.com/default.txt
Integration with Postfix
For Postfix, add the following lines to /etc/postfix/main.cf:
smtpd_milters = inet:127.0.0.1:8891
non_smtpd_milters = $smtpd_milters
milter_default_action = accept
milter_protocol = 2
Start OpenDKIM and configure it to start on boot, then restart Postfix:
service opendkim start
chkconfig opendkim on
service postfix restart
Integration with EXIM
For EXIM, edit /etc/exim/exim.conf and add to the remote_smtp transport:
remote_smtp:
driver = smtp
dkim_domain = $sender_address_domain
dkim_selector = default
dkim_private_key = ${if exists{/etc/opendkim/keys/$sender_address_domain/default}{/etc/opendkim/keys/$sender_address_domain/default}{0}}
dkim_canon = relaxed
dkim_strict = 0
Start OpenDKIM and EXIM, and configure them to start on boot:
service opendkim start
chkconfig opendkim on
service exim restart
Testing
Allow DNS changes to propagate before testing. Use Mail Tester to verify your DKIM setup.
With these steps, you’re all set to ensure your emails are signed and trusted!